Spam! Annoying. Right? Replica watches, designer suits…. some items that cannot be mentioned otherwise we may hit Google with the wrong search terms and attract the wrong audience. Yes spam is annoying, however rarely destructive. Email security solutions were primarily designed to prevent spam. At Carden IT Services we have tried and tested many of the products on offer from many of the different vendors with mixed results. From all of these we located flaws in the solution such as false positives, spam slipping through the net and downtime caused by insufficient resources on the providers networks. Then the game changed. With the fairly new and very destructive type of infection out in the dirty air known as Ransomware, the requirements for email security have changed.
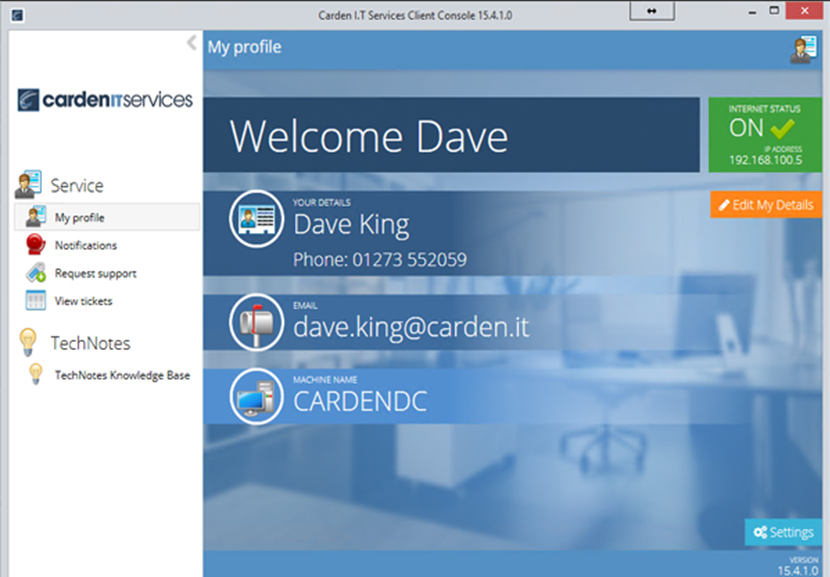
Introducing the Carden Support Client – Extending Our Support Services and Improving the Client Experience
Although our support team are obviously super efficient in responding to your tickets, there have been common questions since we started our company, “Can I log my ticket online?” and “Can we view our ticket updates online?”. Now, with the introduction of our Proactive and Fully Managed IT support packages this has now been produced in the name of the Carden Support Client.
Backup Success! Great! But Restore Success? Have You Tried, Tested and Documented?
There has been a huge evolution in backup technology in recent years. In the traditional backups that were mainly to tape we simply backed up files and folders which could be restored. Sound great? No. For us IT admins it was a nightmare if a system completely failed and needed to be restored from the ground up. In short, it would involve us spending hours if not days reinstalling the operating system and carrying out a disaster recovery of applications one by one, many times the text book procedure would fail and we would have to start the entire process all over again. With the introduction of virtualisation this improved somewhat as we could snapshot the machine before moving onto the next stage, giving us the chance to go back to that point if required. Still far from ideal when you’re up against the clock OR having to provide disaster recovery planning, testing and documentation.
Inbound Solutions – The Cost of Missing Calls
Do you know how many calls your business is missing every day? Do you know the cost of those missed calls? New research has revealed that SMEs in the UK are losing £90 million in potential sales per year as a result of failing to answer calls.
iPhone Error 53 Fix on 6 and 6s
Apple has released an update which has seen a lot of iPhone 6 and 6 Plus users receive an Error Code 53, which essentially bricks the phone.